SMRTe PKI Proxy
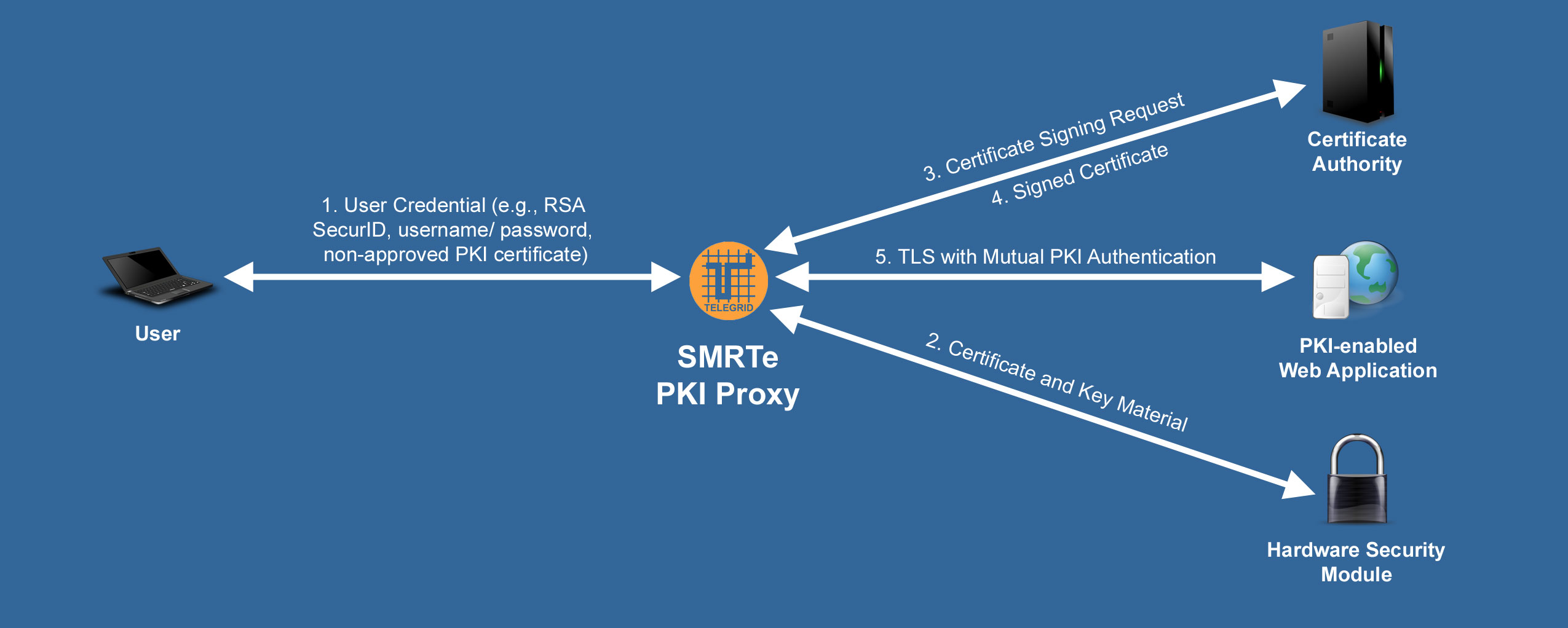
Public Key Infrastructure (PKI) is the most secure method of providing Multi-Factor Authentication (MFA) and information flow in modern networks. PKI certificates combine an individual’s identity information with cryptographic information that is non-forgeable and non-changeable. They provide a standards-based representation of the individual’s physical identity in electronic form and enable data sharing among appropriate, broad and dynamic communities of interest. TELEGRID’s SMRTe PKI Proxy (P/N: RWP-1801) was designed to seamlessly allow the use of PKI certificates in an existing infrastructure.
PKI with Mutual Authentication
PKI with Mutual authentication ensures the integrity and confidentiality of devices and resources operating on a network. It also enables management of identities operating in groups or certain roles within systems. Due to the issues of managing user PKI certificates many organizations only implement server side certificates for secure TLS communications. The SMRTe PKI Proxy accepts any user credential type and automatically generates a unique PKI certificate that can be used for mutual authentication and authorization.
Short Term PKI Certificates
One of the major issues with the management of PKI certificates is revocation or removing the rights of individuals who have left an organization. The reason is that the validity period of PKI certificates is normally two years so revocation lists must be updated and disseminated quickly. The SMRTe PKI Proxy resolves this issue by allowing the dynamic generation of short term certificates drastically reducing the revocation attack vector.
NIST 800-63-3, Holder of Key and Break and Inspect
In June 2017, the National Institute of Standards and Technology (NIST) released the NIST 800-63-3 Digital Identity Guidelines. For the most secure systems the NIST 800-63-3 guidelines require that a user present a proof of key ownership, otherwise known as Holder of Key, in addition to an authentication token. Currently the only standards based method to implement Holder of Key is through X.509 PKI Certificates. This is an issue for organizations that do not implement PKI or implement a Break and Inspect tool which breaks a TLS connection at a network barrier. The SMRTe PKI Proxy dynamically creates user specific PKI certificates to allow Holder of Key.
For more information on Holder of Key and how to seamlessly implement PKI in your organization download TELEGRID’s white paper on Authentication Token Cybersecurity and NIST 800-63-3.
Download the SMRTe PKI Proxy Flyer to Learn More |