
Let’s say you just finished building an amazing sensor. It …

Last month the New York Times published a now famous …

TELEGRID uses Machine Learning in many of its products specifically …
When I first heard of the Robot Operating System (ROS) …

Growing up I had a friend who was into Amateur …

Let’s face it, when it comes to hacks we have …

The General Data Protection Regulation (GDPR) just went into effect …

Adversarial Artificial Intelligence or Adversarial AI is the new buzzword …

Last week Senators Ron Wyden and Claire McCaskill released a …

According to Verizon’s 2017 Data Breach Investigations Report (DBIR), “81% …

While at a recent industry event I heard a senior …

In June 2017, the National Institute of Standards and Technology …
Active Directory has long been a favorite target for hackers. …

This week we received news of another global ransomware attack …

On May 11th President Trump signed a Presidential Executive Order …

Forbes Magazine had an interesting article last month about security …

Every once in a while I read an interesting cybersecurity …

The Mirai Botnet Distributed Denial of Service (DDoS) attack of …

Last week, while driving, an advertisement came on the radio …

LinkedIn Phishing – Are your employees safe? It all started …

PwC released its Global State of Information Security® Survey 2017 …

What Ryan Lochte Can Teach Us About Selling Cybersecurity Tools

Do cybersecurity vendors consider user experience? We need to start …

The DoD CIO Terry Halvorsen made a bold call for …

Every day there are new headlines about stolen passwords. Multi-Factor …

I recently returned from the AFCEA Defensive Cyber Operations Symposium …

TELEGRID was pleased to host a Town Hall meeting by …

Recent advancements in quantum computers have the potential to break …

Authentication is the next battleground of cyberwarfare but as opposed …

There is an interesting story in the Bible about Moses …

What can Cam Newton teach us about embedded software cybersecurity? …

TELEGRID is pleased to announce the release of its 10 …
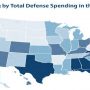
The Department of Defense released its report on defense spending …

In the past two weeks TELEGRID engineers gave presentations on …

Interesting article from CRN about how Software Defined Networking (SDN) …

The Defense Information Systems Agency (DISA) has just released their …




































