Authentication Token Cybersecurity
and NIST 800-63-3
The National Institute of Standards and Technology (NIST) is a federal agency that issues cybersecurity guidelines which are a requirement for federal agencies. In June 2017, NIST released the NIST 800-63-3 Digital Identity Guidelines.
NIST 800-63-3 covers all aspects of Identity and Access Management from initial risk assessment to deployment of federated identity solutions. As opposed to earlier guidelines, which relied solely on authentication type (e.g., single-factor, hard token, etc.) to determine system access, NIST 800-63-3 included Assurance Levels for Identity Proofing (IAL), Authenticator Type (AAL) and Federated Architecture (FAL).
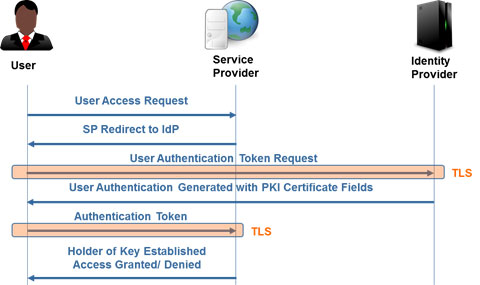
For the most secure systems, those that are deemed FAL3, the NIST 800-63-3 guidelines require that a user present a proof of key ownership, otherwise known as Holder of Key, in addition to an authentication token. This was instituted because relying solely on authentication tokens exposes the network to several cybersecurity attacks including Man-in-the-Middle, Compromised Tokens, Denial of Service, Assertion Repudiation and User Re-authentication.
Currently the only standards based method to implement Holder of Key is through X.509 Public Key Infrastructure (PKI) Certificates as shown below. This is an issue for organizations that do not implement PKI or implement a Break and Inspect tool which breaks a TLS connection at a network barrier. For information on how to seamlessly implement PKI in your organization download TELEGRID’s white paper on Authentication Token Cybersecurity and NIST 800-63-3 Holder of Key.
Single Sign-On and Holder of Key
[goal id=”1455″] |